Instructions how to secure ISPConfig administration of VPS server on Debian 8 using Let's Encrypt certificate.
The basis of VPS server is to properly set machine identification through hostname. In ISPConfig it is necessary to set primary hostname through System>Server options Config and in the Hostname column specify the specific domain, which will be identifying for the server. In our case we will use the fictitious example.com.
Prerequisites for correct functionality
- ISPConfig must be accessible via server IP address - must verify , whether after entering the address https://xxx.xxx.xxx.xxx:8080 the ISPConfig login screen actually displays.
- ISPConfig must be set in SSL availability mode. If not it is necessary to runispconfig_update.sh and enable the SSL option.
- The server address example.com must have DNS A records identical with the server IP address.
If all are done, we can proceed to the settings.
1.Creating the primary SITE server
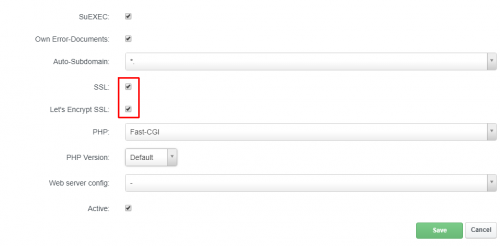
In the ISPConfig administration create a new site via Sites> ;Add new website. This must match the hostname of the server (example.com). When creating it is necessary to check the SSL option a Let's Encrypt SSL.
ISPConfig will generate a certificate for the primary domain and it should be correctly accessible at https://www.example.com< br />
2. Setting certificates for Let's Encrypt
In this step we will "submit" the certificates generated for the primary domain example.com administration ISPConfig. So, we log in to the server via SSH and make a backup of the existing certificate that ISPConfig uses.
cd /usr/local/ispconfig/interface/ssl/ mv ispserver.crt ispserver.crt-$(date "%y%m%d%H%M%S").bak mv ispserver.key ispserver.key-$(date "%y%m%d%H%M%S").bak if [ -f "ispserver.pem" ]; then mv ispserver.pem ispserver.pem-$(date "%y%m%d%H%M%S").bak fi .com
ln -s /etc/letsencrypt/live/example.com/fullchain.pem ispserver.crt
ln -s /etc/letsencrypt/live/example.com/privkey.pem ispserver.key
cat ispserver.{key,crt} > ispserver.pem
chmod 600 ispserver.pem
administration ISPConfig available under the address https://example.com:8080 in secure mode.I have successfully used the instructions to among others also on WEDOS VPS servers.
Problems with SSL certificate
It may happen that the domain that is aliased to the certificate expires or for some reason DNS A records change and Certbot is not able to generate a new certificate.
We start to localize the problem directly from the source, which is /etc/apache2/sites-enabled where the vhosts domain configurations are. In the / files *.vhost is so specified, where the certificate can be found on the server disk. Thanks to this we find that the SSLCertificateFile item sets the path to the certificate and this we need to check if there is a valid newly generated certificate at its end.
We check where the symlinks go in the folder /var /www/domena.tld/ssl/ and specifically symlinks for files:
- domena.tld-le.crt
- domain.tld-le.key
- domain.tld-le.bundle
Mostly go to /etc/letsencrypt/live/domain .tld-XXX/ as a reference to another symlink, which must be checked again. Mostly points to ../../archive/domain.tld -XXX/.
>Generally, the point is that it sometimes happens to me that the automatically generated certificates set the symlinks to the wrong (old) directory, even though the new the certificate has been generated with a new number in a new directory.Usually it is enough to correct the symlinks directly in /var/www/vasedomena.tld/ssl/ and point them to the latest directory in /etc/letsencrypt/live/domain.tld-XXX/. After fixing the symlinks it is required restart apache.
service apache2 restart